Over the Weekend, Sansec reported the news of almost 2000 Magento Online Stores being hacked.
As per Sansec’s early breach detection system, which effectively monitors the global eCommerce space for any security threats, it detected 1904 distinct Magento stores with a unique keylogger (skimmer) on the checkout page.
It’s estimated that the private information of tens of thousands of customers had been compromised over the weekend via one of the compromised stores.
What caused this attack?
As per security experts, it was a typical Magecart attack, which included injecting malicious code to breach, intercept, and log the payment information (card details) of trusted store customers.
The code was injected into stores’ source code to list out payment card details that shoppers entered inside checkout forms.
During the monitoring phase, Sansec found the following data:
- 10 stores got infected on Friday (11th September)
- 1058 on Saturday (12th September)
- 602 on Sunday ((13th September), and
- 233 on Monday (14th September).
With almost 2000 Magento stores jeopardized, the event is described as the ‘Largest Campaign Ever’ by security researchers.
However, most victimized stores didn’t have any history of security incidents, which implies that a new attack method was implemented to gain server access to all these stores.
While Sansec still investigates to find the exact vector that started this largest documented campaign to date, it’s currently being assumed that it may have been related to recent Magento 1 0day (exploit) that was put for sale a few weeks ago.
A user with z3r0day (username) on a hacking forum announced to sell a Magento 1 ‘remote code execution’ exploit method, inclusive of an instruction video for $5000. To sweeten the deal, the user also pledged to sell only 10 copies of the dangerous exploit.
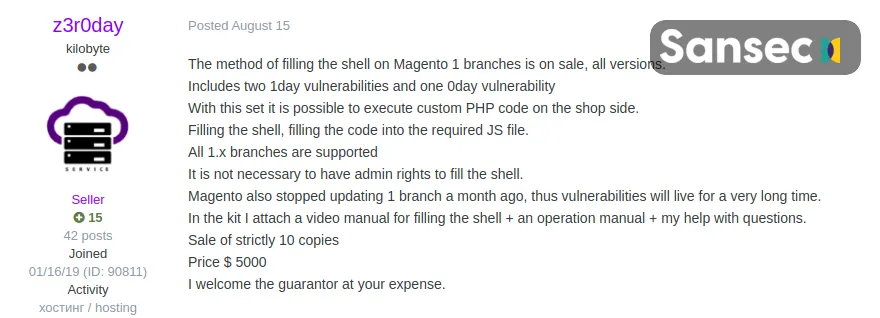
Image Source: Sansec
What made Magento stores Vulnerable?
The inspection conducted by Sansec reveals the hacked stores were operating on Magento version 1, which reached its end-of-life on June 30, 2020.
Magento 1 End of Life refers to the fact that the official Magento team won’t be providing any support quality fixes or updates on security patches to the M1 eCommerce store owners.
After the release of Magento 2 in November 2015, Magento committed to a time of 36 months to offer Magento 1 support, which was further extended to 55 months. Post this, Magento urged and recommended merchants to migrate to Magento 2 platform as soon as possible.
“If you have a store that continues to run on Magento 1 after June 30, please be aware that from that date forward you have increased responsibility for maintaining your site’s security and PCI DSS compliance. Beyond the EOS date, Adobe will not be responding to any further security issues for Magento 1.”
Source: Magento
In case you’re still running your eCommerce site on Magento 1 platform and relying only on web application firewalls (WAFs) to stop breaches and attacks, that’s risky and may not be a wise decision in the long run.
Our M1 EOL Action Program is curated specially for Magento 1 merchants to help them the flexibility to continue using the platform in a secure ecosystem until they migrate to M2.





















